MANAGED CYBER SECURITY
Cyber Risk Management Program
Whether you're a privately held non-regulated entity or a larger organization beholden to one of the compliance frameworks, our team of trusted cyber security experts and partners has you covered
Cyber Risk Management Program
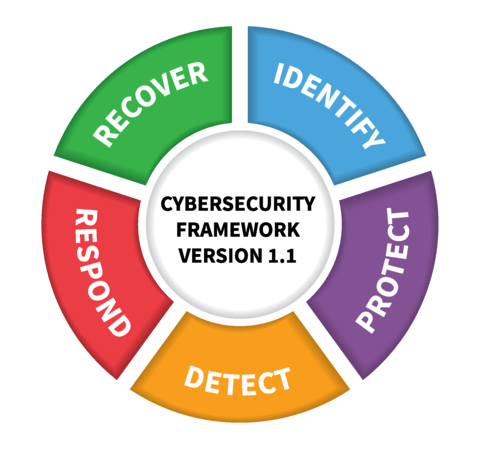
The Phoenix 2.0 Cyber Risk Management Program is based on The NIST Cybersecurity Framework of computer security guidance for how private sector organizations in the United States can assess and improve their ability to manage, prevent, detect, and respond to cyber risk and attacks.
For each phase of the framework we have a list of recommended tools, polices, solutions that clients should have in place given their industry, size and scope. We derive a risk score of their existing security posture as measured against security industry best practices. All of this is easily turned into an on-going living Cyber-Risk Management Playbook, which in turn rolls up into your organization’s Business Continuity Plan. For smaller organizations we have an Essential 12 list of controls and practices which with minimal cost and impact on day-to-day operations will significantly reduce the risk of a severe event.
Cyber Risk Management Examples
- Helping a fast growing startup client whose board, upon receipt of a large funding round, required them to implement policies and controls on company-owned equipment and the runaway fleet of BYOD (bring your own device) devices.
- Helping a client get prepared for and pass a PCI level 3 audit by re-architecting the corporate network and AWS VPC and putting in place data classification and governance policies, thus helping them secure a key underwriting agreement with a national insurance carrier.
- A not-for-profit that does social and political advocacy work received threats from a nation-state with very advanced cyber capabilities and hacktivists alike. Phoenix 2.0 is helping the client implement technical defenses and strategic policies to manage these and other risks
- An in-home health care agency that works with the developmentally disabled population was concerned about threats arising from Business Email Compromise (BEC), we implemented anti-malware and phishing protection, conducted user security awareness and HIPAA training
Besides the above examples,
Cyber Security Programs designed and managed by Phoenix 2.0 have helped clients pass security audits from companies such as Amazon, Merck Pharmaceutical, First Republic Bank and Twitter.

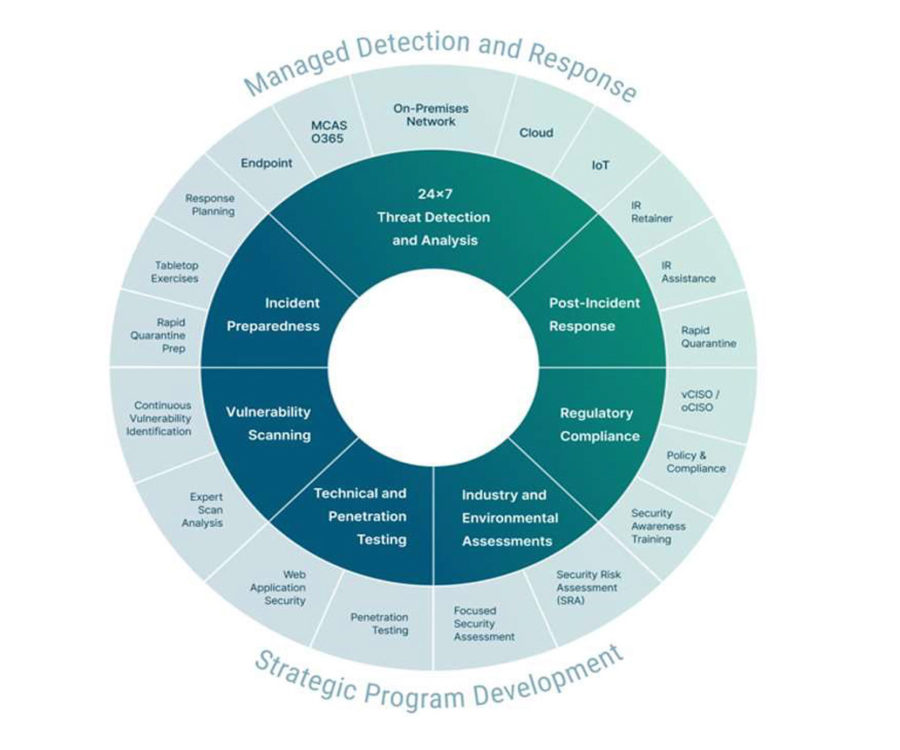
Additional Information Security Services we provide:
- Executive Cyber Risk Posture Reports for Boards, M&A & Investor Due Diligence/Fundraising
- 24/7 Monitoring & (SOC) Security Operations Center
- On-Call Security Experts
- MDR (Managed Detection and Response)
- IR – Incident Response and Remediation
- Assessments: Gap and Readiness Assessments against most common frameworks, e.g. (SOC, ISO, CMMC, NIST, PCI, HIPAA, HITRUST, FEDRAMP, etc.)
- Vulnerability and Penetration Testing
- Industry Compliance
- vCISO/oCISO
- Security Awareness Training
Powered By Critical Insight

Risk Assessment
Has your organization conducted a cyber risk assessment?
Do you have a security strategy and a way to assess and prioritize emerging cyber risk?
Will your controls and governance help you avoid or effectively respond to and recover from a RansomWare attack or other forms of data breach?
In today’s world of rampant RansomWare and with the blurring of technology, workflow and business processes, the risk to your organization is immense and can easily be fatal. The preventative and contingency measures that can help you stave off, or recover from, a breach (or other critical event) are surprisingly low in cost for the ROI and value they provide.
Imagine your computer network taken down or important data being held in a ransom attack that takes your business weeks or months to fully recover from and affects your profit for the year; in addition to damaging your relationships with clients, vendors and regulators.
On the other hand, imagine being attacked and having systems in place so that you are able to continue day to day operations without significant impact. With our Essential 12 plan in place, you’ll feel more secure and be insuring yourself from significant impact and losses. [Read Cost of a Data Breach]
Phoenix 2.0 has a proprietary framework for conducting risk assessments that is expedient, un-intrusive and will give you situational awareness and a plan for action.
During our risk assessment we assess your technical, physical and administrative controls and give you an honest appraisal of your current state, any gaps, what the future state should look like, industry best practices and what it will take to get there. We find that most organizations can significantly reduce their risk by following some basic best practices. We can share templates of policies and help you customize a program to suit your organization.
We’ve placed senior security professionals at many household name companies and silicon valley enterprises, learn more at IT Staffing. Phoenix 2.0 has the skills required to assess and implement straightforward everyday best practices for small to medium local organizations and architect secure enterprise grade infrastructure for bigger, more advanced environments.
Please reach out to us for an assessment of your security today: alex@p20inc.com, 415-